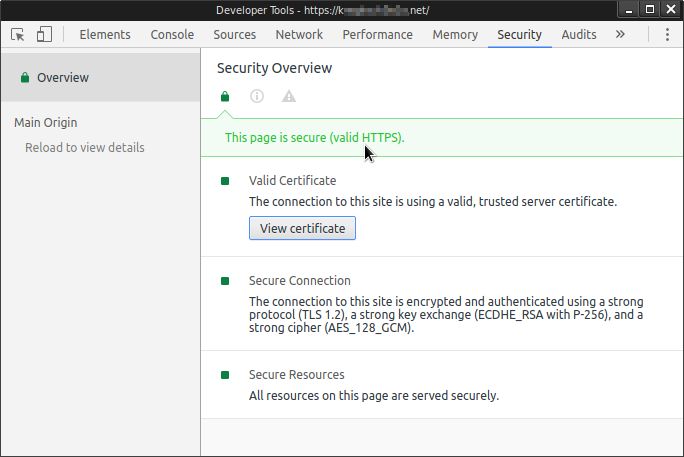
Satisfy Chromium/Chrome 58+ strict requirements for self-signed HTTPS/SSL cert
Create CA key and cert
# openssl genrsa -out server_rootCA.key 2048 # openssl req -x509 -new -nodes -key server_rootCA.key -sha256 -days 3650 -out server_rootCA.pem
Create server_rootCA.csr.cnf
# server_rootCA.csr.cnf [req] default_bits = 2048 prompt = no default_md = sha256 distinguished_name = dn [dn] C=DE ST=Berlin L=NeuKoelln O=Weisestrasse OU=local_RootCA emailAddress=ikke@server.berlin CN = server.berlin
Create v3.ext configuration file
# v3.ext authorityKeyIdentifier=keyid,issuer basicConstraints=CA:FALSE keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment subjectAltName = @alt_names [alt_names] DNS.1 = server.berlin
Create server key
# openssl req -new -sha256 -nodes -out server.csr -newkey rsa:2048 -keyout server.key -config <( cat server_rootCA.csr.cnf )
Create server cert
# openssl x509 -req -in server.csr -CA server_rootCA.pem -CAkey server_rootCA.key -CAcreateserial -out server.crt -days 3650 -sha256 -extfile v3.ext
Add cert and key to Apache2 site-file, HTTPS (port 443) section
SSLCertificateFile /etc/apache2/ssl/server.crt SSLCertificateKeyFile /etc/apache2/ssl/server.key
Copy server_rootCA.pem from the server to your machine..
# scp you@server.berlin:~/server_rootCA.pem .
Add cert to the browser
Chromium -> Setting -> (Advanced) Manage Certificates -> Import -> 'server_rootCA.pem'
YOU ARE ALL DONE!
P.S. Instead of creating a functional CA & server cert pair (per the instructions above) you could simply disable HSTS headers in your HTTP server config.
This will prevent Chromium from enforcing HTTPS and will allow users to click “Advanced → proceed to your.url (unsafe)” without having to obtain and install your custom CA (server_rootCA.pem) certificate. In other words – having to disable HSTS will allow your site to be publicly viewed over HTTP and/or insecure HTTPS connection (beware!).
For Apache2 add the following to site-file, HTTP (port 80) section
Header unset Strict-Transport-Security Header always set Strict-Transport-Security "max-age=0;includeSubDomains"